AH (Authentication Header) and ESP (Encapsulating Security Payload) can be used together in an IPsec (Internet Protocol Security) framework, though it’s not very common in practice. Here’s how they can be combined and the potential benefits:
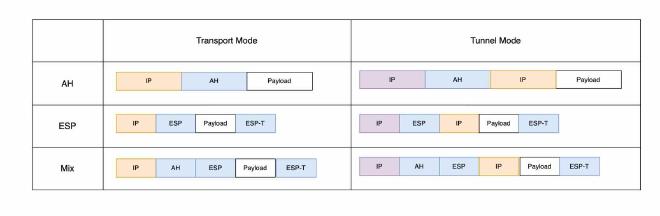
Combining AH and ESP #
In IPsec, you can establish Security Associations (SAs) where both AH and ESP are applied to the same traffic flow, but this usually requires separate SAs for each. The typical configurations would be:
-
ESP in Tunnel Mode + AH in Transport Mode: ESP is applied first to encrypt the entire packet, then AH is applied to provide authentication and integrity check for the outer IP header.
-
AH in Tunnel Mode + ESP in Tunnel Mode: Both AH and ESP are applied in tunnel mode. This configuration encapsulates the packet twice, once with AH and once with ESP.
Benefits of Using AH and ESP Together #
- Enhanced Security: By using both AH and ESP, you get the benefits of ESP’s encryption (confidentiality) along with AH’s strong integrity and authentication capabilities.
- Double Protection: In scenarios where security is of utmost importance, having both encryption (from ESP) and additional integrity/authenticity checks (from AH) can be desirable.
- Compliance and Policy Requirements: Some organizational or governmental policies may require the use of both protocols for certain types of data or communications.
Considerations #
- Performance Overhead: Using both AH and ESP introduces more processing and bandwidth overhead due to the additional headers and processing requirements. This might affect the network performance.
- Complexity: The configuration and management of security associations become more complex when both AH and ESP are used together.
- Limited Use Cases: In most practical scenarios, ESP alone is sufficient, as it provides confidentiality, integrity, and authentication (if combined with a suitable authentication algorithm). Therefore, the additional use of AH is often unnecessary.
- Compatibility Issues: Some NAT (Network Address Translation) devices have trouble passing AH traffic because AH is designed to protect the integrity of the entire packet, including the IP header, which NAT may need to modify.
In conclusion, while it’s technically feasible to use AH and ESP together in IPsec, the decision to do so should be based on specific security requirements and a thorough understanding of the implications, including the impact on network performance and compatibility. In many cases, ESP alone, particularly with modern encryption and authentication algorithms, is sufficient to meet security requirements.
